Published at January 31, 2024 · Krystian Hebel · 7 min read

This post shows how we tested simple commands on TwPM, which is our attempt at making TPM more open....
Published at January 31, 2024 · Krystian Hebel · 7 min read

This post shows how we tested simple commands on TwPM, which is our attempt at making TPM more open....
Optimizing SPI communication on STM32 MCUs: a comprehensive guide to high-frequency communication
Published at July 28, 2023 · Artur Kowalski · 22 min read
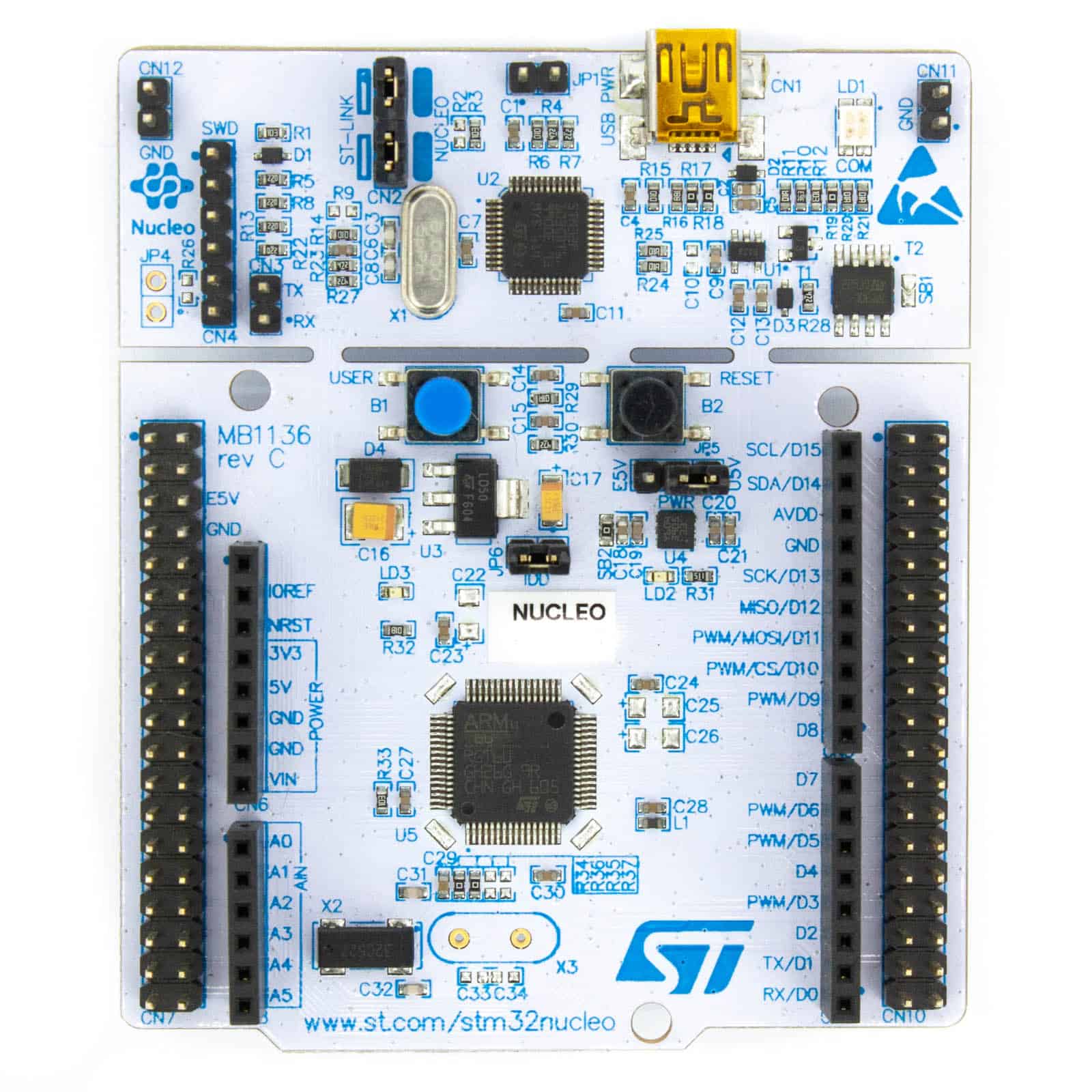
In this blog post, we delve into the fascinating world of Serial Peripheral Interface (SPI) on STM32 microcontrollers (MCUs). Specifically, we explore how SPI is utilized in TPM chips for communication with PC motherboards. We encounter the challenges of achieving high-frequency SPI communication, especially when operating as a slave, and the specific limitations of STM32L476 MCUs. The article further uncovers the limitations of existing approaches in platforms like Zephyr and STM32 HAL. We then embark on a journey to fix SPI issues, improve DMA performance, and optimize the firmware for high-speed SPI communication. Throughout the blog post, we provide in-depth technical insights and share valuable test results. Join us as we push the boundaries of SPI communication and unlock new possibilities in the world of microcontrollers....
Categories: firmware miscellaneous security
Fobnail Token - example use case
Published at May 19, 2023 · Krystian Hebel · 11 min read

This phase focused on using Fobnail in a real-life use case, namely using it to access LUKS2 decryption key if and only if the PCR measurements are valid...
Categories: security
Published at June 23, 2022 · Tomasz Żyjewski · 7 min read

The Fobnail Token is an open-source hardware USB device that helps to determine the integrity of the system. The purpose of this blog post is to present the development progress of this project. During this phase, we focused on researching OS for hosting Fobnail Attester...
Categories: security
Fobnail Token - Fobnail provisioning
Published at May 25, 2022 · Krystian Hebel · 9 min read

This phase is about provisioning Fobnail Token itself. The closing point of that process is creating a certificate for Token that can be used later after attestation succeeds...
Categories: security
Fobnail Token - platform attestation
Published at April 6, 2022 · Artur Kowalski · Krystian Hebel · 6 min read

The Fobnail Token is an open-source hardware USB device that helps to determine the integrity of the system. The purpose of this blog post is to present the development progress of this project. This phase was focused on attestation....
Fobnail Token - platform provisioning
Published at March 21, 2022 · Krystian Hebel · 7 min read

The Fobnail Token is an open-source hardware USB device that helps to determine the integrity of the system. The purpose of this blog post is to present the development progress of this project. This phase was focused on platform provisioning....
Published at October 8, 2021 · Michał Kopeć · 5 min read
An introduction to TPMs. Let's explore the differences between common implementations of TPMs and how they might matter to you....
Proof of concept implementation of RATS attestation for the TrenchBoot
Published at December 14, 2020 · Norbert Kamiński · 9 min read

This blog post will describe the concept of the IETF Remote Attestation Procedures (RATS) and implementation of CHAllenge-Response based Remote Attestation (CHARRA) with TPM 2.0 for TrenchBoot....
Qubes OS and 3mdeb 'minisummit' 2020
Published at May 15, 2020 · Kamila Banecka · 5 min read

Once again, we will meet on QubesOs & 3mdeb minisummit 2020 discussing #QubesOS, #firmware, #coreboot, #security and #TPM related topics. All the event details are presented in the following blog post....
Categories: firmware miscellaneous security
Qubes OS and 3mdeb 'minisummit' 2019
Published at August 7, 2019 · Piotr Król · 8 min read

In May we had pleasure to meet Marek Marczykowski-Górecki #QubesOS Project Lead in 3mdeb office in Gdańsk. We discussed various #QubesOS, #Xen, #firmware, #coreboot, #security and #TPM related topics. Results of that "minisummit" was presented in following blog post....
How to mitigate ROCA TPM vulnerability?
Published at April 17, 2019 · Krystian Hebel · 10 min read

ROCA vulnerability was discovered (October 2017) in a software library, RSALib, provided by Infineon Technologies. That library is also used in TPM modules. When this vulnerability is present, a pair of prime numbers used for generating RSA keys is chosen from a small subset of all available prime numbers. This results in a great loss of entropy. Details and exact numbers can be found here. UPDATE 2021-10-20: provided new link for TPM firmware updates (old one was no longer working), added info about patch for openssl-1....
Published at February 23, 2019 · Marta Szelecka · 2 min read

3mdeb at Embedded World 2019 We are excited to inform You that 3mdeb will take part in embedded world Exhibition & Conference - Embedded World 2019 next week! In place full of enthusiasts You can meet us personally between 26.02-28.02 in Nuremberg, Germany. Come and talk with us about amazing world of embedded systems. We will tell You not only about our work and innovations, but also share our knowledge, help and present to You our products and demos:...
Categories: miscellaneous