PSEC 2019 enables hardware/firmware engineers, VMM/OS developers, architects, integrators, verifiers and senior technical staff to collaborate on hardware-assisted platform security and composable software supply chain integrity, from edge to cloud. Piotr Król, 3mdeb founder and Embedded Systems Consultant was one of the speakers with the article “Less-Insecure Network Edge Virtualization with Low Size, Weight and Power” and shared with us his thoughts and notes, which will be published here in the next weeks.

The event started 1 Oct in Redmond, WA, at Microsoft Studio B with 3 introductional videos which were meant to bring the participants into more exalted mood. The most interesting of the videos touched the areas of necessity of support for organizations like NASA that rise the level of knowledge in all the mankind. It was also related to the power of stories, myths, that push our species growth. Next all the presentations took place as planned. We’ll gonna shorten the most interesting ones. Reader can find all the abstracts on the conference page.
“Guarding against physical attacks; Xbox” Tony Chen
Imagine, that your task is to create a nuclear shelter. It should be safe and secure but also easy accessible for anyone with proper key. And it should be located on the hostile territory.
This was essentially the problem with one of the most attacked devices in history. When you are working on PC security you can assume, that your job is to protect the PC owner and his stuff from outer threats. You can consider him being a good guy. On the contrary to the Xbox the owner is a threat himself. It is him, who will probably try to use software and hardware tools to compromise it. Why should he? Because it may give him an advantage in online games or enable piracy.

Modern gaming platforms are priced below the manufacturing cost. Companies want to rather earn their share with software - games designed for specific platform. That’s why they consider eventual piracy an extremely dangerous threat. It may be a matter of company existence - the best example is SEGA.
There are two ways to make a device recognize tampered optical disk as a genuine one. The first one is to make the disk absolutely identical - which can be obtained but is not a part of the scope of this article. The second one is to make a device recognize not-exactly-identical disk as the original one. This is the place where an physical attack can be performed.
The device is controlled by the attacker. Silicon die inside the CPU has 28 nm, this size makes it not economically feasible to modify. This is the reason why CPU should be the only trusted component. Any other hardware can’t be trusted because the owner can connect something simulating its behavior to proper bus. As a consequence we can’t trust to any data from flash, SSD, HDD, ODD, DRAM. Moreover, have to assume, that every PIN was exposed and attacked. Attacker can use whatever he wants with any tools to manipulate with connections between any parts of hardware. If we don’t want to become paranoid we should come back to the economical feasibility. Yes, there are some invasive silicon attacks methods that will successfully pass almost every security walls, but let’s assume, that our attacker won’t spend thousands of dollars to buy tools used for analysis and debugging by semiconductor manufacturers. Microsoft stated that threat modding game have to be more expensive than 10 games - about $600. So what have they actually done?
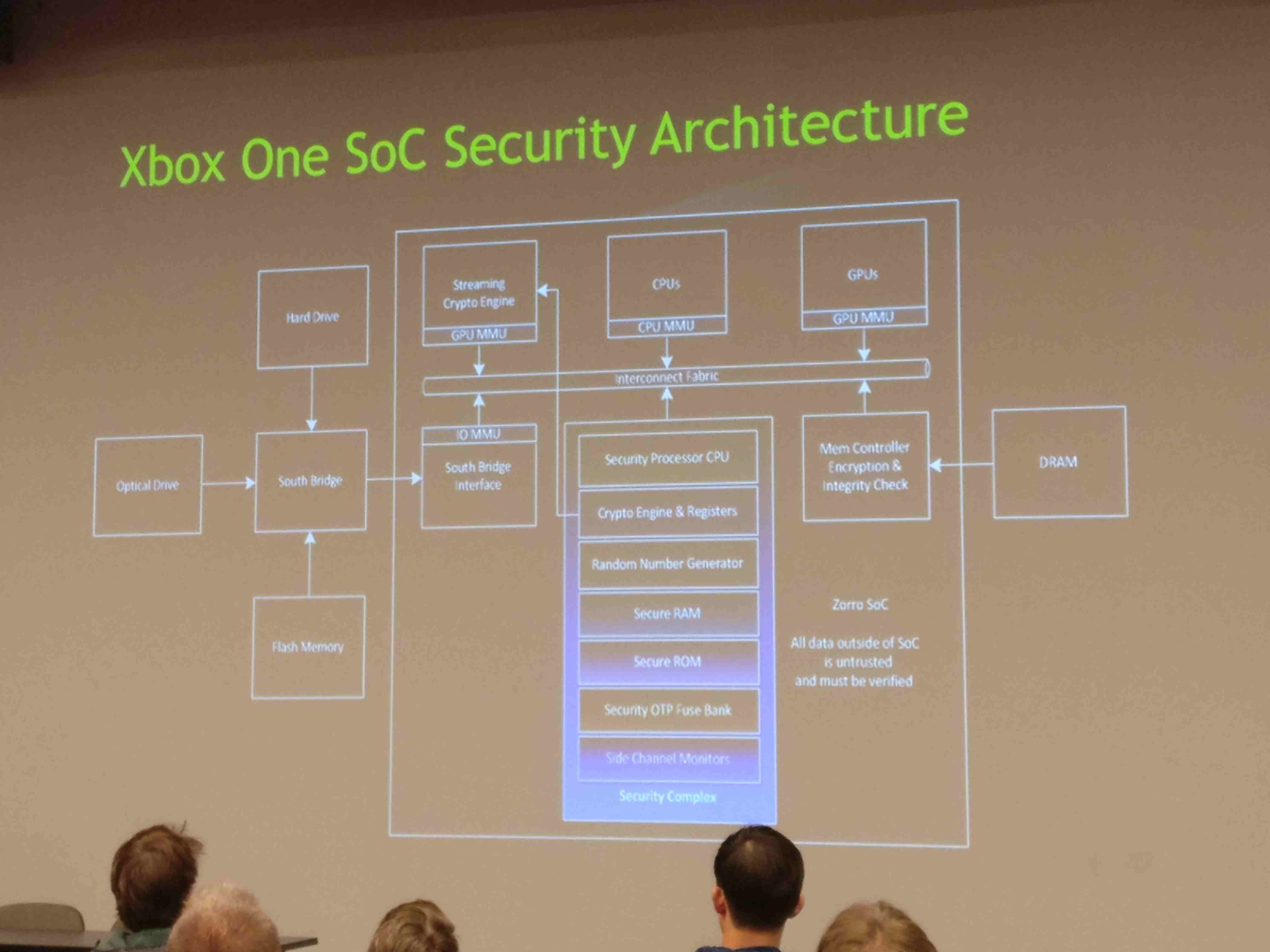
The key was adding another security layer. Security processor - separated chip that enforce fuse revocation as well as anti-rollback mechanism - that manages secure boot process. It contains custom registers called PCR (just as in TPM) which are used to store hashes for every bootstage. OS integrity is checked at boot time. Global key can be accessed only at boot ROM stage and there is no way to access it further. The chain of trust is constructed in a way that keys are available only at stage they are needed, then they disappear and cannot be used at different boot phases. Global key gives ability to encrypt first stage bootloader. Global key is related with game decryption. First game is decrypted by CPU and then stored encrypted with different key in DRAM.
After boot Xbox split OS into separate partitions - read-only and read-write. While read-write partitions are empty from the beginning, the read only partition integrity is checked and comes from XVD binary file. XVD files can’t be modified, and during upgrade they are just replaced with the new one, which means that cold boot of the platform brings it to the trusted state.
Then Chen described how using sophisticated methods and tools these security features has been successfully broken. A group of individuals bought several Xbox platforms for research purposes and tried to scrape layer after layer from the silicon chip to reveal proprietary architecture. They have designed a scheme of the points where to drill and selective destroy areas that leverage platform security. Exact datasheets were obviously not shown.
Summary
These materials were presented the first time for an open audience, though they are six years old. Security methodology about keys and verification of further phases is very similar to RIoT architecture that Microsoft ties to DICE. Chen claimed this is Azure Sphere architecture (what is unverifiable at the time). Below you can watch the full lecture video.
If you think we can help in improving the security of your firmware or you
looking for someone who can boost your product by leveraging advanced features
of used hardware platform, feel free to book a call with
us or
drop us email to contact<at>3mdeb<dot>com. And if you want to stay up-to-date
on all things firmware security and optimization, be sure to sign up for our
newsletter:


