Introduction
JTAG port is an important feature that helps a lot of engineers during product development. It also may be helpful for adversaries while performing a reverse-engineering process - e.g. is a chance to dump the memory of your firmware and get access to strictly confidential information. In this article, we show how to lock JTAG access for users who don’t have a special key. We will use Secure JTAG feature which is implemented on i.MX SoC’s. In our lab, we tested Secure JTAG settings on i.MX6 but this same feature is available on a lot more NXP platforms. Unfortunately, some part of NXP documentation is not publicly available.
Requirements
-
Development board: Any i.MX6 devkit with available JTAG port. It can be Sabre lite i.MX6 from Boundary Devices (218,66 EUR).
-
SoC reference manual: Setting JTAG in secure mode is a dangerous operation - if you miss something or will be wrong with any fusebit name or the address you can enable unexcepted options. Always work with documentation - here is application note about JTAG modes.
-
crucible tool: JTAG mode and access key are saved in fuse bits - we need software to manipulate fuses in userspace. crucible tool can be used for that - it is the best of free and open-source tools with a huge database of fuse fields. With that tool we can burn fuses using their names - it is more safety than counting banks and words.
-
JTAG compatible with OpenOCD: On NXP sites we can read that Secure JTAG is supported only by the Lauterbach environment and ARM-DS5 IDE with DSTREAM debugger. In 3mdeb we are always trying to use open-source software. Unfortunately, OpenOCD doesn’t officially support Secure JTAG in i.MX SoC’s, but we found not accepted yet patch from 2014 which adds support for work with SJC (System JTAG controller) in a secure mode. Required patch work on OpenOCD from official repository if you checkout code with
970a12aefhash. There is a chance to apply patch in the actual version of OpenOCD, but it needs some code changes. As hardware, we used ARM-USB-OCD-H (54,95 EUR) from Olimex.
The simplest way to use OpenOCD with SJC patch is to use our fork. You only need clone our repository, build and install OpenOCD:
|
|
- System image: Any Linux image for your i.MX6 platform with kernel module
nvmem-imx-ocotpfor modifying OTP memory. You can add this module in menuconfig by enabling the optionCONFIG_NVMEM. NVMEM driver can be built as a module and loaded only when you want to burn fuses.
How it works
SoC’s from i.MX family offers JTAG in three modes
-
No debug - security on the highest level, but after disabling debug possibilities development and debugging via JTAG port will be unavailable permanently on used device
-
Secure JTAG - mode described in this article, the best compromise between security and development possibilities - only person with an access key can use JTAG
-
Enabled JTAG - default mode, enabled for anyone who has physical access to JTAG pins
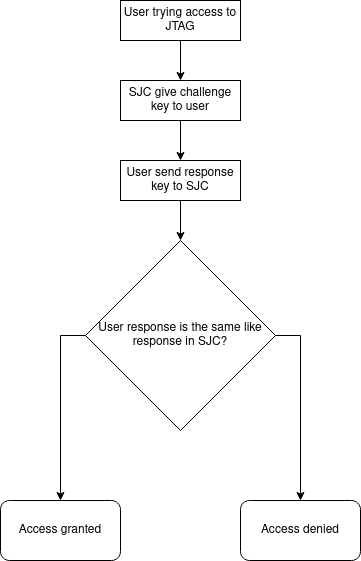
Secure JTAG mode is based on a challenge/response mechanism. SoC has a unique
challenge key saved during manufacturing. User can generate their response
56-bit key and burn it in JTAG fuse named SJC_RESP. While trying to access the
JTAG port, SJC gives a unique for any device challenge key. Now user should pass
the response key which is compared with the response stored in SoC fuse bits. If
keys are the same, JTAG is enabled. Below, you can see a diagram describing the
challenge/response mechanism.
JTAG mode can be set in JTAG_SMODE fuse by values
| Mode | JTAG_SMODE | |————-|————| | JTAG enable | 0x0 | | JTAG secure | 0x1 | | No debug | 0x2 |
These fuses still can be overwritten until we do not block this possibility -
the response key can be locked by writing 0x1 to SJC_RESP_LOCK, and JTAG
mode with all other fuses from BOOT group by writing 0x3 to BOOT_CFG_LOCK.
Now JTAG fuses should be protected from writing and overriding. There is an
option to set this to locking only override - look at the reference manual or
application note
for more information about fuse overriding feature.
Setting up
Using crucible
Get the latest prebuild release from
official project page
(on the day of writing our article it is v2021.12.17). You can also download
source code and build it by yourself - this process is described in
readme. Crucible
program doesn’t require any specific installation procedure - just remember to
give access to execute binary file.
Run crucible on your target and check that you have access to fuse bits from
userspace
|
|
We can see that JTAG is set in default mode - JTAG enabled for everyone. Now
let’s try to set secure mode. We generate a random response key:
0x00574c200308fad77 and save it into SJC_RESP
|
|
Now we can change the mode to secure JTAG
|
|
OpenOCD with i.MX secure SJC patch use imx6_sjcauth.txt file to store access
keys. We can get the challenge key during the first try of connection. Let’s try
|
|
Works fine, now a response key is required to access JTAG. It looks like we can lock JTAG related fuses: mode and key. They should be unavailable to override now.
|
|
It is time to verify our solution - remove line with key from imx6_sjcauth.txt
and try to connect again:
|
|
JTAG access is disabled now if you do not have a file with the correct response key. In OpenOCD output, we can see that debugger sees the challenge key but cannot authenticate and connect to the SoC.
Using U-boot
There is a possibility to fuse JTAG from U-boot shell - for that fuse prog
command can be used. You will need to build bootloader with enabled
CONFIG_CMD_FUSE config. More description of fuse functionality is
here. It
is a more common solution, but you need to use banks and words numbers instead
of fields names. If you enter incorrect numbers you may brick device, so we
recommend using crucible.
Summary
Secure JTAG mode is a very useful feature, which should be implemented in every device where security is important. JTAG can be an open door for whole system architecture: while debugging device adversary can dump memory of program which can be critical for your system infrastructure. If you do not pay attention to encryption and other safeguards someone can read important and confidential data like passwords and addresses.
If you think we can help in improving the security of your firmware or you
looking for someone who can boost your product by leveraging advanced features
of used hardware platform, feel free to book a call with
us or
drop us email to contact<at>3mdeb<dot>com. And if you want to stay up-to-date
on all things firmware security and optimization, be sure to sign up for our
newsletter:
