Recently, the firmware security subject was one of the biggest topics of the IT environment. As of 2018, almost every computer system is affected by the Spectre security vulnerability. To fix mentioned security issue it is necessary to update your platform’s firmware provided by trusted vendor. Many people come out of the mistaken belief that changing the firmware is a very complicated task and fears that they can “brick” their platform or personal computer. Others do not know where to find matching updates. Fortunately, there is a tool that enables secure software updates in a very accessible way - meet fwupd, an open-source daemon integrated with LVFS.
LVFS - what does it mean?
The Linux Vendor Firmware Service is a secure portal that brings
together firmware updates uploaded by renowned hardware vendors. The LVFS
provides reliable firmware alongside with the detailed metadata for clients such
as GNOME Software or fwupdmgr. Hosting or distribution of mentioned content
is cost-free, so if your hardware vendor is not on the list, feel free to ask
what they think about joining this project. Then there is a possibility to
request an account on the LVFS site, get legal permission to redistribute the
firmware and start uploading new updates.
Single upload contains binary file and at least one XML file with required metainfo about target device and firmware, all packed as a cabinet archive, which is consistent with the Microsoft Update requirements.
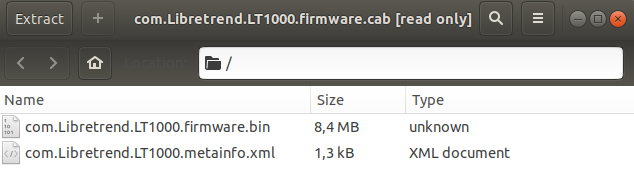
Archives specially prepared by authorized vendors are the key to the whole update process. Metadata from the LVFS brings the details about available updates to the user together with patch notes description. The XML file needs to meet the structure and content standards which can be found in the LVFS examples.
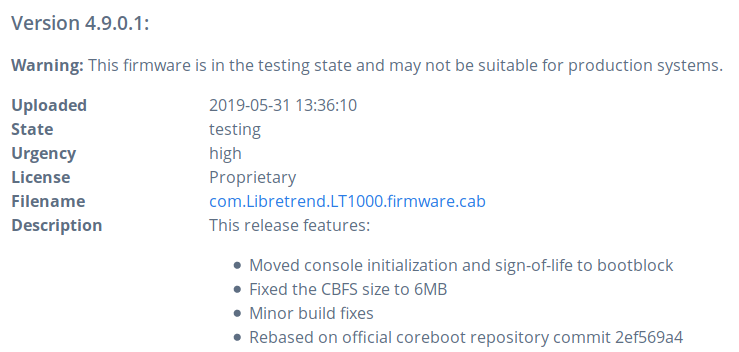
Example of v4.9.0.1 coreboot release for Libretrend LT1000:
|
|
We can announce, that from the beginning of 2019 we are approved ODM for
Libretrend company and our status can be tracked on LVFS vendor list.
Until now we have uploaded 4 custom firmware versions: v4.8.0.2, v4.8.0.3,
v4.8.0.4 and the newest v4.9.0.1 specially refined coreboot for Librebox
platforms (LT1000).
Fwupd - end user’s powerful tool
The fwupd project provides a system-activated daemon fwupd - program that runs
as a background process and in this case, with a D-Bus interface that can be
used by unprivileged clients. End users have an option to use command line tool
called fwupdmgr which enables firmware updates via Linux terminals or even on
the headless clients via SSH protocol.
The daemon creates a device with a unique ID and the provider assigns a number of GUIDs to the device - these are used to match a binary file to a device with the identification numbers from the metadata. Users can be uncertain if their hardware is supported by OEMs and LVFS - to be sure there is a list showing all the updates that have been pushed to the stable metadata.
Last week we got the permissions to promote our binaries from private
“embargoed” state to testing and stable repositories, which are open to the
public! If You are interested in updating your Librebox computer, check uploaded
binaries with release notes of each fixes and changes.
After making sure that platform is supported by fwupd/LVFS, users have a wide
choice of fwupdmgr options to run - all of them are listed with
fwupdmgr --help:
|
|
Typical firmware updating process using Linux terminal looks like this:
- Login to your system.
- Refresh LVFS metadata from the remote server:
fwupdmgr refresh - Check available updates:
fwupdmgr get-updates - Update firmware to the newest version:
fwupdmgr update - Reboot your system and check installation result:
fwupdmgr get-results
See for Yourself the fwupd capabilities in the quick asciinema demo:
As you can see, above process is “painless and easy”, because required preparations regarding binary files and security check are done by approved providers.
Fancy plugins
The fwupd project supports a great number of plugins:
| Plugin | Supports |
|---|---|
| ColorHug | custom HID protocol |
| CSR | Cambridge Silicon Radio protocol |
| Dell | various devices on Dell hardware |
| DFU | reads and writes data from USB devices supporting the DFU interface |
| Logitech | Unifying protocol |
| SynapticsMST | updating MST hardware from Synaptics |
| Thunderbolt | Thunderbolt controllers and devices |
| UEFI | adds devices found on the system and schedules an offline update |
| WacomHID | Wacom update protocol |
| Flashrom | In the near future! |
In the help from fwupd developers, we (3mdeb) have integrated libflashrom API
creating a new way of running flashrom plugin relaying on always up-to-date
flashrom library, rather than simply calling subprocess with hardcoded full
command. More information about flashrom plugin capabilities and upstreaming
process can be tracked in this PR.
The conclusion
Despite the complexity of the LVFS and fwupd infrastructure, updating firmware with fwupd daemon is quite simple. There is now plenty of supported machines ready to be more secure and reliable in the everyday tasks. I hope that after this lecture, firmware updating process is not scary anymore and anyone willing to update their platform will try this individually.
Want to know more about this open-source project or just simply trying to contribute your priceless code which enables new, needful plugins? Check the LVFS website.
If you think we can help in improving the security of your firmware or you
looking for someone who can boost your product by leveraging advanced features
of used hardware platform, feel free to book a call with
us or
drop us email to contact<at>3mdeb<dot>com. And if you want to stay up-to-date
on all things firmware security and optimization, be sure to sign up for our
newsletter:
